Table of Contents Show
Here I am going to talk about some hacking techniques (cyber security) most commonly used by hackers to hack your Facebook, Gmail, Twitter, or any account on the internet you have. So that you could aware of these techniques and always be alert whenever someone tries to hack your account.
But if you are not aware of these powerful hacking techniques (cyber security) then you may be hacked by any hacker and become a victim. So read all the techniques very carefully and double-check your system or environment if you feel something bad then must take action to prevent yourself to be hacked.
Phishing
Phishing is the oldest and most commonly used hacking trick, In this technique hacker creates a replica website of the most popular website like Facebook, Gmail, Twitter, linked, etc, and hosts this duplicate website on any server with a subdomain like http://facebook.example.com and sent this link to the victim with some attractive message. As soon as the victim clicks on the link and tries to log in on Facebook. Then victim’s username and password are mailed to the hacker’s email id or stored on the hacker’s database. So always check the URL on the browser address bar after that use login and be safe.
These are common social media cyber security threats:
Session Hijacking
Session Hijacking is also one of the dangerous hacking techniques if you are accessing any popular website on a non-secure (http://) connection. HTTP means the website does not have an SSL certificate to secure your communications on the Internet, so always look for HTTPS on the websites you visit.
In this technique, the hacker hacks the victim’s browser cookie which is used to authenticate the user’s connection on the website and the hacker uses the victim’s cookie to gain access to their account. Session Hijacking is the most commonly used over LAN or wifi networks. There are lots of session hijacking tools available on the internet, Firesheep is one of the very popular packages for session hijacking.
Keylogging
This is the easiest way to hack a user’s account password. Keylogging software is very dangerous even if you have good knowledge about computers, In this technique, hackers install Keylogging software on the victim’s computer, and Keylogging records all actions and keystrokes taken by the victim and all logs sent to the hacker’s email id.
Mobile Phone Hacking
Today everybody uses a smartphone we installed apps from all the popular websites, And accessing their account via apps makes things easier but sometimes it is also dangerous if how hackers to gain access to control a victim’s smartphone, there is a tool called meta exploit which designed for penetration testing these tools have lots of payload for android phone using these payloads hacker can take control of victim’s smartphone and record victim’s action over phone. So don’t install unknown sources of apps on your phone.
Password Stealer
Almost everybody uses stored passwords in their browser to access their account. This is quite convenient, but can sometimes be extremely dangerous. Password stealers are software specially designed to capture the saved passwords stored in the victim’s Internet browser. So try to avoid saving your password on the browser.
USB Hacking
You may have listened about this technique, If an attacker has the privilege to access your computer, Then the attacker stores some auto-run software in his/her pen drive, and as soon as the attacker inserts a USB drive in the user’s computer, A password Stealer program automatically runs and user’s all saved password will be stored attacker’s USB drive.
DNS Spoofing
If both the victim and attacker are on the same network, an attacker can use a DNS spoofing attack and attacker create a fake page on the website for example he/she change the original Facebook page to his own fake/duplicate page and Whenever victim tries to log in on their Facebook page via hacker’s fake page you may get hacked. This technique works over LAN and WiFi.
Social Engineering is a simple attack made by hackers, in this method hackers collect information about victims as much as they can from various methods. If the victim has a simple password like his birth date, mobile number, school name, girlfriend’s name, pets name, etc, A good hacker can easily judge your account password and may hack your account, So don’t share your all information to anyone and try to make your password more strong how much your password will strong hacker may not judge your password easily.
HTML Source Code Hacking
If you have saved your account password on the browser and if the attacker used your computer then he/she can view your saved password on the browser setting and also can view the password by changing the source code of the page using firebug or inspect element feature of the browser attacker can easily change <input type =”password”> into <input type =”text”> via HTML source code. See the image.
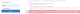

Cyber security is the most important part of our life as day by day people are used to technology-based services whether in the form of websites or gadgets, hence social media cyber security threats become part of our life.







